A Security Mechanism for Clustered Wireless Sensor Networks Based on Elliptic Curve Cryptography
1National Hsinchu University of Education, Hsinchu, Taiwan
2Ralink Technologies, Hsinchu, Taiwan
3Micrel Semiconductor Inc., San Jose, California, U.S.A.
Abstract
The data communications in wireless sensor networks are susceptible to eavesdropping and tampering due to the open communication environments. Limited by the hardware of sensor nodes, it is difficult to use complicated encryption methods for the design of defense mechanisms. Thus, the security issues in wireless sensor networks are mainly focused on symmetric key encryption (SKE) methods, which have lower computational complexity but limited connectivity and scalability. In this study, a security mechanism based on elliptic curve cryptography (ECC) is proposed to provide the authentication for sensor identity and message transmission. The mechanism uses certificates to examine the entity status for the defense against multiple attacks in clustered wireless sensor networks. Its confidentiality and integrity are verified by a network security analysis.
1. Introduction
A wireless sensor network (WSN) is formed by one or more base stations and a large number of sensor nodes to monitor the objects of interest or environmental conditions such as sound, temperature, light intensity, humidity, pressure, motion and so on through wireless communications. Recently, the advance in micro-electro-mechanical systems (MEMS), embedded processing, and battery technology have facilitated the development of low-cost and low-power sensors with the functions of sensing, wireless transmission, computation and data processing.
As the technology of wireless sensor networks matures, the scope of their applications has become more extensive, e.g., environmental monitoring, home automation, intelligent office, energy saving, intelligent transportation, health care, and security monitoring. Since the sensor nodes are deployed in open communication environments, they can easily be attacked during data transmission. To prevent confidential information from being stolen, it is important to provide secure communications between sensor nodes and base stations.
Due to the limited computational resources in sensor nodes, the public key cryptography (PKC) is not applicable in wireless sensor networks in comparison with the symmetric key or non-public-key encryption methods. The symmetric key encryption (SKE) has a lower complexity but is less flexible than the PKC. Besides, the SKE must ensure a secure key transmission at the first-time communication, which incurs additional overhead and the waste of storage space. Also, the SKE uses the same key for encryption and decryption, which may cause the whole network to be controlled once the attackers have obtained the key and thus it is not suitable for a large wireless sensor network.
The PKC is an asymmetric encryption method using a public key and a private key to perform data encryption and decryption. Most PKC and digital signature algorithms are related to the RSA algorithm [1], a non-symmetric key encryption algorithm proposed by Rivest, Shamir and Adleman in 1977. The RSA algorithm is based on the safety of integer factorization problem (IFP). The RSA algorithm must use a longer key length to achieve a higher security, and it also incurs more computational complexity. Compared with the RSA algorithm, elliptic curve cryptography (ECC) only requires a small number of key bits to achieve the same degree of security [2-4]. Therefore, ECC has a computational advantage over the RSA algorithm especially when applied in a hardware-restricted environment [5].
A large wireless sensor network may contain thousands of sensor nodes, so the SKE is less flexible because it requires higher communication bandwidth and a larger memory space. As the technology of sensor hardware continues to progress, ECC becomes feasible for the PKC [6, 7]. According to Krzysztof’s experiments [8], the power consumption using the PKC has no significant impact on the lifetime of sensor nodes.
In this paper, a key management mechanism based on ECC is proposed to provide authentication services for the identity and message transmission. The mechanism uses certificates to examine identity status for the defense against multiple attacks in clustered wireless sensor networks. Its confidentiality and integrity is verified by a network security analysis.
2. Related Research
In this section, the routing protocols often used and the network attack patterns commonly found in wireless sensor networks are described. In addition, the key distribution and management mechanisms based on the security requirements of wireless sensor networks are also included.
2.1 Hierarchical Routing
An important challenge in wireless sensor networks is limited communication bandwidth and electric power. Using the hierarchical architecture can increase network scalability and thus reduce the communication overhead, delay time as well as complexity in management. Hierarchical architecture adopts the concept of clustering by dividing the sensing environment into several regions to reduce communication overhead. When doing so, the sensor nodes are grouped into clusters after deployment and each cluster contains a cluster head and some sensor nodes responsible for sensing and transmitting data to the base station. The cluster head can also perform data aggregation to reduce the amount of data before transmitting the data to the base station.
Some routing protocols in wireless sensor networks are described in the following. The low-energy adaptive clustering hierarchy (LEACH) proposed by Heinzelman et al. [9] is a well-known hierarchical routing protocol applied in clustered wireless sensor networks. LEACH divides a wireless sensor network into a number of clusters, and sensor nodes in the same cluster can communicate with each other directly. A sensor node decides which cluster to join based on the strength of received signals. After joining a cluster, sensor nodes in the same cluster randomly select a cluster head for collecting and forwarding data to the base station (Figure 1). Since the cluster head will consume more energy, it has to be replaced regularly to reduce the power consumption.
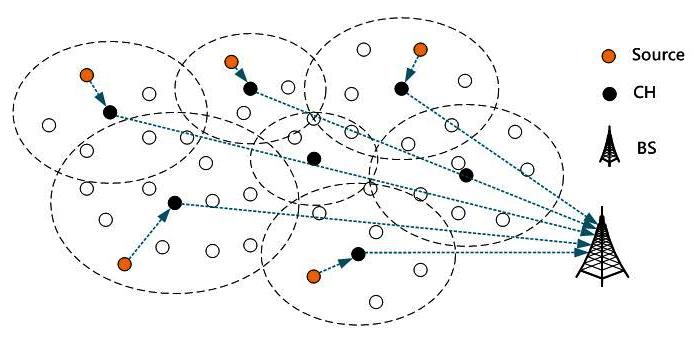
Figure 1. LEACH’s hierarchical routing architecture
To replace LEACH’s distributed operation by a centralized control, LEACH-Centralized (LEACH-C) was proposed by Handy et al. [10] and it is more effective in extending the lifetime. In the deployment phase, each sensor node sends back its location to the base station. Then, the base station selects cluster heads according to their power conditions and positions, and the selected cluster heads start to transmit data to the base station afterwards. This approach can effectively extend the lifetime of LEACH, but its drawback is that distant cluster heads will consume power quickly.
Manjeshwar and Agrawal proposed the Threshold sensitive Energy Efficient sensor Network protocol (TEEN) [11], which can immediately react to unexpected events. TEEN is based on LEACH to send back sensor data to the base station periodically, and it sets two threshold values, i.e., hard threshold and soft threshold, to avoid the transmission of duplicated sensor data. This method can save electric power, but it is not applicable in the environment requiring periodical data as the threshold values may not be met in occasion.
For the improvement of TEEN, Manjeshwar and Agrawal proposed the Adaptive Periodic Threshold sensitive Energy Efficient sensor Network (APTEEN) as a revision [12]. APTEEN remedies the drawback of TEEN by reporting data periodically, and the objective is to react to sudden events in real time. After the sensor network is established, each cluster head sends out four parameters:
- Attribute: information about data events.
- Thresholds: including hard threshold and soft threshold.
- Schedule of TDMA (Time Division Multiple Access): every sensor node will receive its own allocated time slot.
- Count Time: the time interval between two transmissions. When the count time is reached, the data will be transmitted as a periodical report.
2.2 Attacks in Wireless Sensor Networks
Using the hierarchical architecture is more efficient in saving power, but it also has some disadvantages, such as liable to selective-hole attacks and replay attacks. In the following, some attacks commonly found in wireless sensor networks are described.
A. Replay Attack
The attackers intercept encrypted packets with signatures and resend them without making any changes, so the receivers consider them as original packets. Using outdated information and the authentication of legitimate identity, the attackers can obtain secret data or useful information. To prevent such attacks, a time stamp or a sequence number can be added to check if the packet has been resent or not (Figure 2).
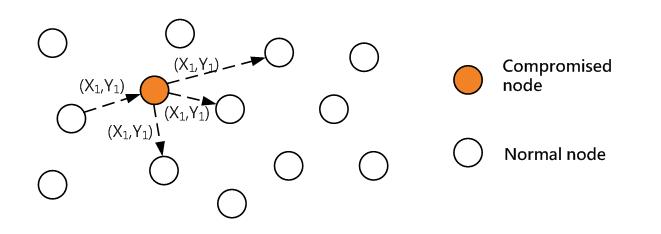
Figure 2. The model of replay attacks
B. Selective Forwarding
After receiving a packet, the attackers selectively forward or not to forward the packet, or just send the packet containing the routing information to prevent it from reaching the destination. In that case, the packet needs to be re-transmitted and the network traffic and power consumption will increase, and thus the lifetime of the entire network is reduced.
C. Sinkhole Attack
A sinkhole attack prevents the base station from obtaining complete and correct data, which may form a serious threat to higher-layer applications. Sometimes, the attackers may gather around the router such that the transmitted data will traverse through the attackers. For example, an attacker may claim that it has a high-quality or low-latency route to the base station for attracting the neighbor nodes to send data through it. When the routes go through the attacker, the data packets may be tampered or the attacter can start attacks to influence the network (Figure 3).
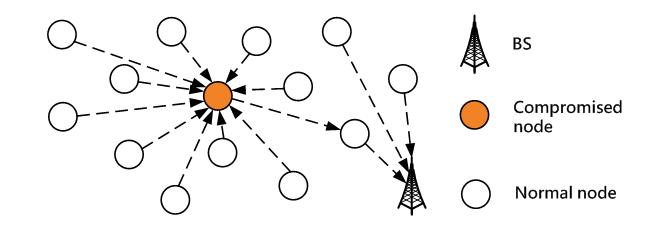
Figure 3. The model of sinkhole attacks
D. Denial of Service (DoS)
There are many forms of DoS attacks, and the purpose is to prevent sensor nodes from providing their services in the networks. The common form of DoS attacks is to block the services by requesting a large number of resources, for example, sending a huge amount of meaningless data to the target network, which will cause users not able to receive the services. As a result, the network can not function properly since the bandwidth has been depleted.
E. Sybil Attack
The concept of Sybil (or multiple-identity) attacks was first proposed by Douceur in P2P networks [13], and it is defined as a single node has multiple identities to disrupt the accordance between entities and physical devices in the networks. A method was proposed using the trusted certification center to verify the physical identity for preventing multiple-identity attacks. The multiple-identity attacks usually use a single malicious node to confuse neighbor nodes, causing chaos among them, and finally the entire network is interfered and thus can not function properly (Figure 4).
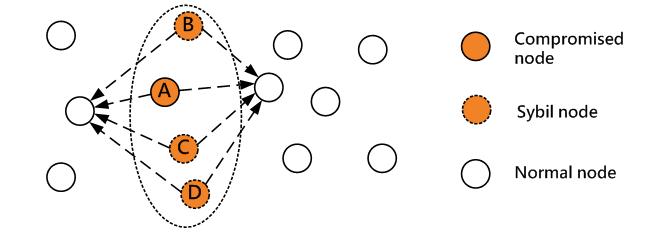
Figure 4. The model of Sybil attacks
2.3 Key Distribution and Management
It is difficult to apply traditional security mechanisms to prevent the above attacks in wireless sensor networks due to limited resources in a sensor node. In recent years, many security mechanisms for wireless sensor networks have been proposed, e.g., using encryption and decryption methods to provide security services such as identity authentication and key management. The latter can be further divided into two parts, i.e., key distribution and key revocation. Basically, key distribution deals with how the keys are distributed among all sensor nodes for secure communication; key revocation is referred to as safely remove the keys from the attacked sensor nodes. Currently, the key pre-distribution method is often used for the key management in wireless sensor networks.
An easy way of key distribution is to use the same key for all sensor nodes (Figure 5(A)). In this way, sensor nodes are pre-loaded with the primary key such that any two nodes can use it for encrypted communication. However, the attackers can control the entire networks if they gain access to the primary key. Another extreme approach is for any two nodes to share a unique key pair (Figure 5(B)). When a node is attacked, it will not affect the security of the other nodes. This method can prevent the entire network from being attacked easily. For a wireless sensor network containing n nodes, each node must store n-1 keys, and the whole network has to store n(n −1) / 2 keys. If n is a large number, this method requires a lot of memory space to store the key pairs.
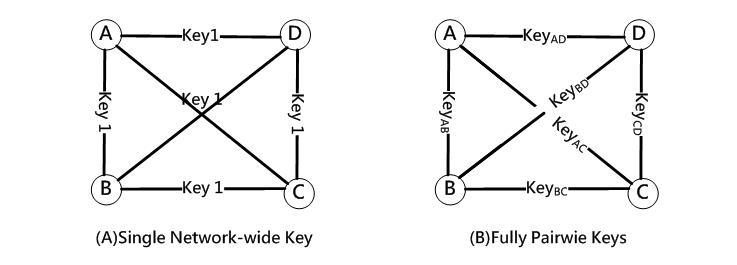
Figure 5. Cases of using a primary key and unique key pairs
The random key pre-distribution methods randomly select k keys from a key pool to establish the key ring for a node, and each key contains the corresponding identity (ID) number. After deployment, each node must broadcast the key’s ID number within its communication range to find out the nodes sharing the same key. Therefore, a secure communication can be established as long as there is at least one key being shared (Figure 6). If there is no shared key between two nodes, the link has to be established through two or more key paths.
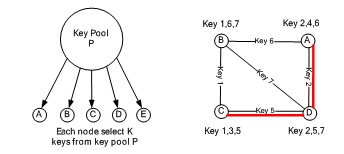
Figure 6. Random key pre-distribution methods
Compared with the fully pair-wise shared key mechanisms, this method requires fewer pre-loaded keys and thus can save the memory space, but it can not verify the identity of neighbor nodes due to multiple links with the same shared keys. Random key pre-distribution methods do not require too much computation time for generating key pairs, but the time for searching the shared keys is proportional to the number of keys. Hence, there is a trade-off between network connectivity and memory space, and a certain number of pre-loaded keys are required to achieve a high connectivity in the network.
Since a sensor node has a higher chance to communicate with their neighbor nodes, a group-based key management mechanism was proposed for deploying sensor nodes [14]. In Figure 7, there are four groups and each group has three nodes. Groups G1, G2, G3 and G4 are called the in-groups, and nodes 1, 2, 3 belong to G1. To allow communications among different in-groups, the nodes in different in-groups are organized into cross-groups. For example, nodes 1, 4, 7 and 10 belong to cross-group G1. In deployment, the nodes within a group can be pre-loaded with the same key pairs to establish a secure communication. This method can reduce the required memory space and achieve a better performance and scalability. However, if a node has to establish secure communication with the cross-group nodes, there is no guarantee that these nodes are within its communication range.
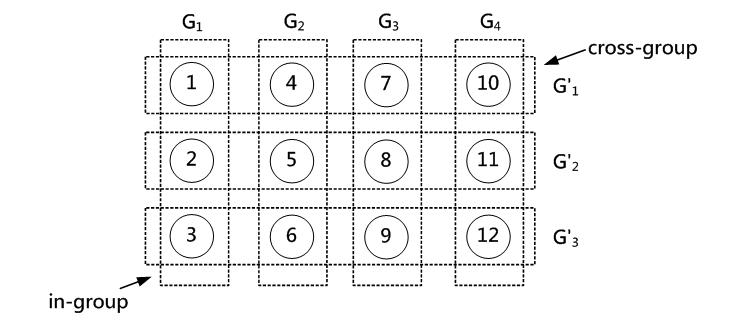
Figure 7. Group-based key management mechanism
2.4 Elliptic Curve Cryptography
The PKC is based on the concepts of public key and private key, and its security is achieved by using digital signature as well as key encryption and decryption to solve the discrete logarithm problem (DLP). At present, a lot of PKC systems are designed based on the RSA algorithm. Elliptic curve is an old mathematic problem, which has been studied in algebra and geometry for a long time. In 1985, Miller and Koblitz proposed to apply elliptic curves to the PKC, including key exchange, encryption, and digital signature, to reduce the computation cost of the DLP.
ECC is based on the characteristics of elliptic curves, so its variables and coefficients are limited to the elements in a finite field, which contains only finitely many elements. Addition and multiplication are the specific operators, by which the result of any two elements is still within the finite field. The finite fields are classified by their size (or order), and there is exactly one finite field up to isomorphism of size pn for each prime p and positive integer n. If the series is defined as p, then the finite field is expressed as Fp . There are two types of ECC:
- The elliptic curve in the finite field Fp is a prime curve if p is a prime number, and Fp is defined as a set of integers{0,1,..., p-1} .
- The elliptic curve is a binary curve in the finite field F2m , where m is a large integer and F2m is defined as a set of integers{0,1,...,2n-1}.
In the applications requiring a
higher security, using ECC prime curves is more efficient than traditional
cryptography [15], so this study is based on the prime field Fp. In general, an elliptic curve E is expressed by the equation ![]() . The elliptic curve E
is defined in the prime field Fp, where the point (x, y) falling into the
elliptic curve E will meet the
equation
. The elliptic curve E
is defined in the prime field Fp, where the point (x, y) falling into the
elliptic curve E will meet the
equation
![]() .
.
The above equation is expressed
as Ep(a,b), where p is a large prime
number and x, y, a, b are the elements of the finite field Fp. Also, a
and b must satisfy the following
equation
![]() .
.
The elliptic curve also
contains a point at infinity, denoted by O. The
order n of an elliptic curve is the
number of all points including the point at infinity. It is necessary for Ep(a,b) to meet the requirement ![]() .
.
A. Rules of Addition
l
O serves as the additive identity. For
any point P on the elliptic curve, it
is true that ![]() .
.
l
If and
, then
![]() .
.
l
For two points ![]() and
and ![]() on
on ![]() , where
, where ![]() , if
, if ![]() , then R is the
intersection point of the
straight line
, then R is the
intersection point of the
straight line ![]() and the elliptic curve Ep(a,b).
and the elliptic curve Ep(a,b).
l
The sum of the same point P is ![]() , and
, and ![]() is the tangent
line through P.
is the tangent
line through P.
B. Rules of Multiplication
Multiplication of a point P by an integer k on an elliptic curve is performed by adding P for k times, defined as
![]() .
.
ECC provides an efficient key-exchange mechanism. Elliptic Curve Diffie-Hellman (ECDH) [16] is the ECC based on the key exchange mechanism, which calculates the shared key using the exchanged public key and private key. First, ECDH picks a large prime number P and selects the base point G = (x, y) from Ep (a,b), where Ep (a,b) and G are public parameters and the order of the base point is a large number n satisfying nG=O. The following example (Figure 8) describes how the keys are exchanged between two users.
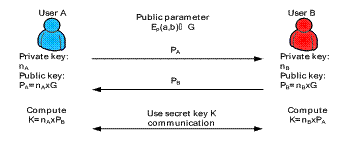
Fig. 8. The operation of key exchange by ECDH.
(2)
User B
selects an integer ![]() less than
the order n as its private key, and
then generates a public key
less than
the order n as its private key, and
then generates a public key ![]() , which belongs to a point on
, which belongs to a point on ![]() .
.
(3)
After
exchanging the public keys, user A generates its private key ![]() and user B generates its private key
and user B generates its private key ![]() . Here,
. Here, ![]() is equal to
is equal to ![]() because
because
![]() .
.
So far, many studies in wireless sensor networks have used ECDH to develop information security methods because it only needs a small key length to achieve the same degree of security as that of the RSA algorithm. Therefore, ECDH is very suitable for applications in wireless sensor networks.
The security of ECC is based on
the solution of DLP. Given a base point G
on Ep(a,b)with order n, it is
feasible to calculate another point Q = kG, where ![]() and k < p by the given k and G. With known Q and G, it is very
difficult to calculate k with limited
time if n is very large. To prevent
the DLP from being cracked, one can use 1024-bit RSA as the baseline security,
and the prime number P must be greater
than 160 bits in the elliptic curve equation. The order n of the elliptic curve base points must also be a prime number
greater than 160 bits
and k < p by the given k and G. With known Q and G, it is very
difficult to calculate k with limited
time if n is very large. To prevent
the DLP from being cracked, one can use 1024-bit RSA as the baseline security,
and the prime number P must be greater
than 160 bits in the elliptic curve equation. The order n of the elliptic curve base points must also be a prime number
greater than 160 bits ![]() . To achieve the same security level, a 160-bit ECC key
length is needed to reach the strength of 1024-bit RSA [4]. Since ECC has the
advantages of a lower computation complexity and storage requirement, the key
management mechanism developed in this study is based on ECC by using 160-bit
key length and the ECDH for key exchange.
. To achieve the same security level, a 160-bit ECC key
length is needed to reach the strength of 1024-bit RSA [4]. Since ECC has the
advantages of a lower computation complexity and storage requirement, the key
management mechanism developed in this study is based on ECC by using 160-bit
key length and the ECDH for key exchange.
3. Defense Mechanism
This study is focused on the design of a defense mechanism against multiple attacks in a two-tiered clustered wireless sensor network (Figure 9). A sensor node may be out of service due to power exhaustion or malicious attacks, so adding new sensor nodes to the network is sometimes necessary. A key management mechanism based on ECC is proposed in this study to provide authentication services for the identity and message transmission of sensor nodes. The mechanism provides the added nodes with pre-loaded public keys as certificates to help the other nodes verify their legitimacy, and these keys can also be used as the shared keys with neighbor nodes. By doing so, the old nodes do not have to update their keys for secure communications with the new nodes.
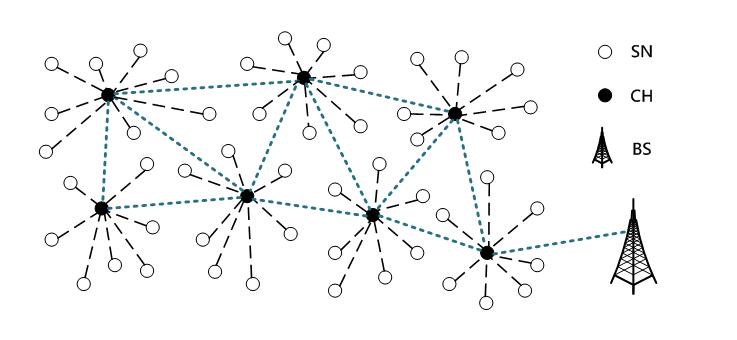
Figure 9. A two-tiered clustered wireless sensor network
3.1 Network Environment
The wireless sensor network under investigation includes a base station, a number of sensor nodes and some cluster heads, and their major functions are described as below:
A. Base Station
The base station is a powerful node in the wireless sensor network and it can reach a wide range of communication area. The base station can be located at any place of the network, and it is not limited by electric power, memory space, or data-processing capacity. The base station serves as the gateway for external communication. If the base station has been invaded then the whole network will be taken over, so it is assumed that the base station is well protected and can always be trusted.
B. Sensor Node
It is assumed that sensor nodes are randomly distributed, and each node has a unique identity number. Sensor nodes are limited by electric power, memory space, computation capacity, and communication range. A sensor node can communicate directly with other nodes in the same cluster, and it has to transmit the collected data to its cluster head.
C. Cluster Head
A cluster head is selected from the sensor nodes in the same cluster, so it has the same capacity and functions as the other nodes. After deployment, the cluster head is responsible for collecting data from the sensor nodes, and the data are then forwarded to the base station. It is noted that a sensor node will not enter the sleep mode when serving as a cluster head.
3.2 Initialization Phase
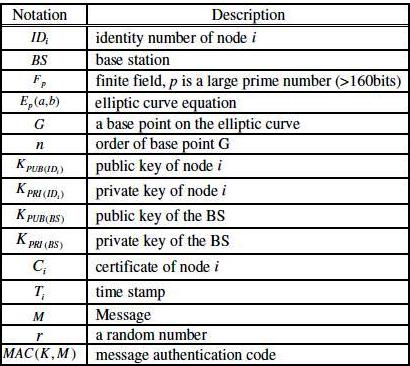
Before deployment, each sensor
node has to go through an initialization phase, in which the base station functions
as the trusted certification authority. The base station generates a pair of
public and private keys for each node, and issues the pre-loaded certificates
to ensure the legitimate identity of the newly added nodes. The base station
will first initialize the system parameters (Table 1) by selecting a large
prime number p and the elliptic curve
parameters a and b to define the elliptic group Ep(a,b). Then, a base point G
is selected from Ep(a,b) with order n being
a large number. The base station has to create the public and private keys for
itself as ![]() and also for each
node as
and also for each
node as![]() , and then store the ID and public key
, and then store the ID and public key ![]() for future usage. Each node is pre-loaded with IDi,
for future usage. Each node is pre-loaded with IDi,![]() ,
,![]() , G, and Ep(a,b), as well as the base station’s public key
, G, and Ep(a,b), as well as the base station’s public key![]() and certificate.
and certificate.
Table 1. Parameters in the key management system
The initialization
steps are shown in the following:
(1)
The BS
plays the role of certificate authenticator by selecting the parameters Ep(a,b), G, P and n.
(2)
The BS
generates a key pair ![]() , identity IDi
as well as certificate
, identity IDi
as well as certificate![]() for each node,
and a key pair
for each node,
and a key pair ![]() for itself. The
BS stores each node’s identity and public key
for itself. The
BS stores each node’s identity and public key ![]() , while each node stores its own identity and the parameters
, while each node stores its own identity and the parameters ![]() .
.
(3)
Each node broadcasts its
identity and certificate ![]() , and the other nodes can use the pre-loaded public key to
verify the legitimacy and validity, and organize themselves into clusters. Then,
each cluster will elect a cluster head.
, and the other nodes can use the pre-loaded public key to
verify the legitimacy and validity, and organize themselves into clusters. Then,
each cluster will elect a cluster head.
(4)
After selecting a cluster head, the
cluster head will apply for a new certificate
from the BS using the existing certificate ![]() . After verifying the validity of the certificate, the BS will
use the cluster head’s public key to encrypt the new certificate
. After verifying the validity of the certificate, the BS will
use the cluster head’s public key to encrypt the new certificate![]() to ensure that
only the cluster head can use the private key
to ensure that
only the cluster head can use the private key ![]() fordecryption to obtain the certificate
fordecryption to obtain the certificate![]() .
.
(5)
Each
node in a cluster will apply for a new certificate from its cluster head
using the existing certificate![]() . After verifying the validity of the certificate, the cluster
head will use the applying node’s public key to encrypt the new certificate
. After verifying the validity of the certificate, the cluster
head will use the applying node’s public key to encrypt the new certificate ![]() to ensure that only the node can use the private key
to ensure that only the node can use the private key ![]() for decryption to
obtain
for decryption to
obtain![]() as the certificate.
as the certificate.
The pre-loaded public key can be used as the certificate to ensure the legitimate identity of newly added nodes. The sensor nodes within a cluster can also verify the legitimacy with each other within the valid period of certificates and then select their cluster head. For example, node A and node B in Figure 10 send their certificates to each other for verification. Because the certificates were pre-loaded with the public key by the BS, each node can verify the validity with each other through the public key.
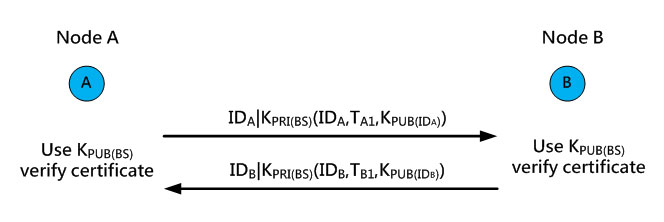
Figure 10. Verifying certificates in the initialization phase
After the deployment, the cluster head can apply for a new certificate from the base station, and the BS will use the cluster head’s public key KPUB(ID) to encrypt the certificate. Therefore, only the cluster head’s private key KPRI(ID) can be used to decrypt and acquire the certificate. When a cluster head obtains a new certificate, it will become the trusted certification center of the cluster, and the other nodes in the cluster can apply for a new certificate from it. In Figure 11, node A has become a cluster head after deployment, and it has to apply for a new certificate from the BS. The BS will issue a new certificate after verifying its validity by using node A’s public key KPUB(IDA) for encryption, so only the nodes with private key KPRI(IDA) can decrypt it to obtain a new certificate.
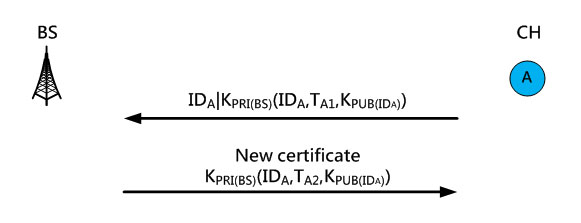
Figure 11.The cluster head applying for a new certificate
When a cluster head becomes the trusted certification center, the other nodes in the cluster can apply for a new certificate from it. The cluster head will verify the certificate, and then use the node’s public key KPUB(ID) to encrypt it and issue a new certificate. For example, node B in Figure 12 applies for a certificate from cluster head A, which will first verify the certificate and then use node B’s public key for encryption to ensure that only node B can decrypt it to obtain the certificate.
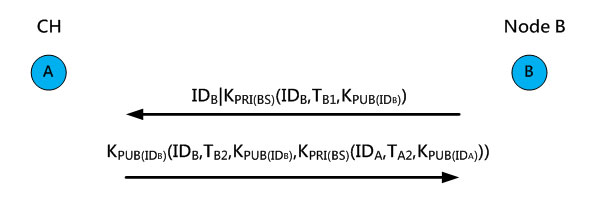
Figure 12.The sensor node applying for a new certificate
In order to extend the lifetime
of wireless sensor networks, the cluster head will be replaced regularly to
average the power consumption among all sensor nodes.
(1)
After reorganization,
the cluster head sends a new certificate ![]() to the BS, and it will receive a new certificate after
verification. The new certificate will be encrypted with the cluster head’s
public key
to the BS, and it will receive a new certificate after
verification. The new certificate will be encrypted with the cluster head’s
public key ![]() .
.
(2)
The
sensor nodes in a cluster must apply their certificates from the cluster head,
and the cluster head will issue new certificates ![]() upon successful validation of their applications.
upon successful validation of their applications.
A newly selected cluster head, e.g., node B in Figure 13, will send its current certificate to the BS for verification, and the BS will issue a new certificate using the cluster head’s public key KPUB(IDB) for encryption. Only the nodes with the private key KPRI(IDB) can decrypt it to obtain a new certificate. Figure 13.
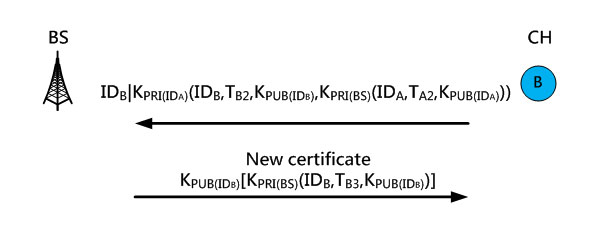
Fig. 13. The cluster head applying for a new certificate
After a new cluster head has been selected, the other sensor nodes have to apply for new certificates from the cluster head again. For example, node A will apply for a new certificate from the cluster head (node B) in Figure 14. Node B will use the public key obtained from the BS to check the validity of node A’s certificate before issuing a new certificate, and then use node A’s public key for encryption to ensure that only node A can decrypt it to obtain the certificate.

Fig. 14. The sensor node applying for a new certificate
3.3 Secret Key Exchange
When two sensor nodes start to communicate, they must send their certificates to each other to ensure the validity of the certificates. After that, they will obtain their mutual public key and use ECDH to calculate the secret key by the following steps:
- Each node will send out its ID and certificate to each other to verify the validity and legitimacy of the certificate, and then obtain the public key from each other.
- Each node uses the other node’s public key and its own private key to calculate the shared key as
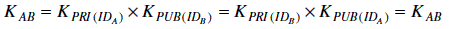
- After calculating the private key, both nodes can use it for secure communications and calculating the authentication code of messages for the integrity of information.
In Figure 15, node A sends out its certificate and ID to node B and uses the public key KPUB(BS) obtained from the BS for verification to obtain node B’s public key. Similarly, node B also sends out its certificate to node A, and uses node A’s public key KPUB(IDA) for encryption. When the verification is completed, they can use the private key and public key to compute the shared private key KAB .
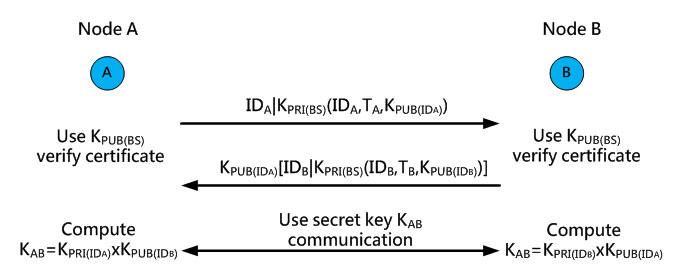
Fig. 15. Obtaining the secret key for secure communication
After obtaining the shared key KAB , both nodes communicate with each other using the secret key, and a random number is added to the transmitted message for verifying its integrity (Figure 16).
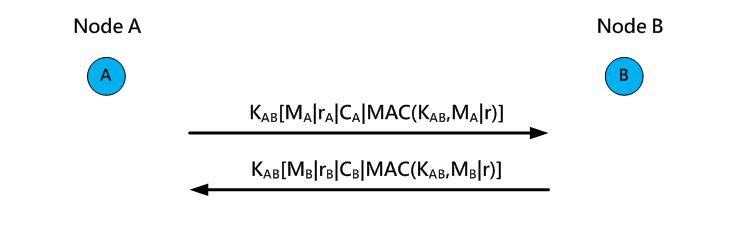
Fig. 16. Using the secret key for secure communication
4. Security Analysis
In wireless sensor networks, the data transmission is more susceptible to eavesdropping and tampering due to open communication environments. The contents of messages may be tampered, causing the BS to receive incorrect information and waste a lot of electric power in transmitting the useless messages. In this section, the confidentiality and integrity of the proposed security mechanism is analyzed for the defense of several attacks.
4.1 Confidentiality
As the messages are encrypted and sent to the recipient, it is important to ensure the confidentiality of each node. The public key encryption method uses the transmitter’s public key to encrypt the messages, and the recipient uses its private key for decryption. Since each node has its own private key, only the recipient can decrypt the messages and thus the data confidentiality is ensured.
The proposed mechanism uses a P2P encryption method for message transmission. Sensor nodes use the shared secret keys with the cluster head to encrypt the messages. The cluster head uses the shared secret key with the base station to encrypt the messages. Therefore, the transmitted messages can only be decrypted with the shared keys to obtain the information. Even being eavesdropped, the attackers do not have the private key to calculate the secret key so they can not decrypt the messages. Even if the attackers control a node in the network, they still can not decrypt the messages forwarded by this node. Thus, this mechanism can ensure the confidentiality of transmitted messages no matter if the network is subjected to internal or external attacks.
4.2 Authentication
To ensure that both the transmitter and the recipient have legitimate identities, the sensor nodes can use the cluster head’s public key to ensure the certificates are generated by a legitimate node and have not been tampered with or forged during the transmission process.
4.3 Integrity
The message authentication code is calculated by using secret keys and then appended to the data for transmission. Therefore, the attackers can not modify or forge the message without the secret keys. Also, the recipient must calculate the message authentication code for verification to ensure that the receivied messages have not been modified. The recipient can use the authentication code to determine if the received message is legitimate, and discard the message if it has been modified. In the following, it is shown that the key management mechanism can be used for the defense against several attacks.
A. Resend Attack
The attacker intercepts the encrypted packets and resends the packets without making any changes. The recipient mistakes the attacker as the node sending out the original packets. Thus, the attacker can use the outdated information to pass the identify certification for obtaining useful messages. In each encryption process, the proposed mechanism will select a different random number to attach with the packets so that the attacker can not use the outdated information to carry out resend attacks.
B. Eavesdropping Attack
The attacker collects data by eavesdropping to obtain secret data or useful information. For the proposed mechanism, the public key and base point G are points on an elliptic curve. The attacker can not derive the secret key even with the public key and base point G since it doesn’t have the private keys to solve the DLP. Besides, the secret information can also be transmitted with encryption and signatures to prevent from eavesdropping. For example, node A and node B in Figure 17 send out the certificates to each other to obtain the public key first, and then transmit the messages with signatures using their private keys. Because the messages are encrypted using each other’s public key, only the recipient has the private key to decrypt them and thus the eavesdropping attacks can be prevented.
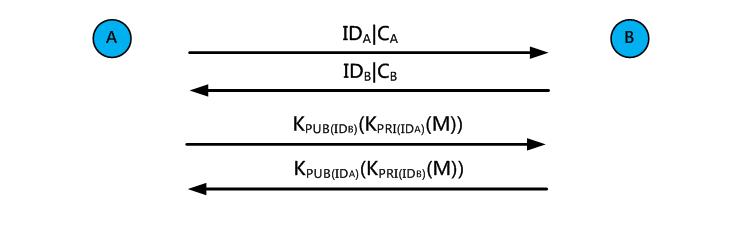
Fig. 17. Defense against eavesdropping attacks
C. Tampering Attack
The attacker transmits tampered authentication messages, causing the recipient to obtain incorrect information. Using the proposed mechanism, the authentication code will be attached to the transmitted packets, and the code is also encrypted using the secret key, which enables the recipient to know whether the packets have been tampered with or not. For example, node A and node B in Figure 18 will first calculate the secret key KAB, and then attach the authentication code calculated by KAB when sending messages. If the attacker tries to tamper the messages, it has to use the secret key KAB to calculate the authentication code or use brute-force attacks to break the code. The latter requires a lot of computation time min(2k ,2n ) , where k is the key length and n is the message length.
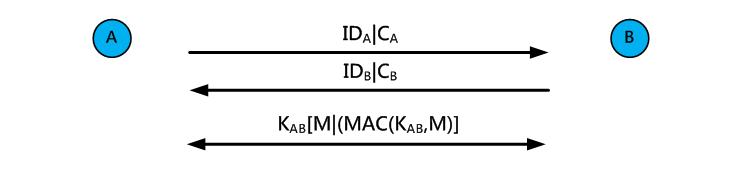
Fig. 18. Defense against tampering attack
D. Multiple Identity Attack
An attacker broadcasts a number of authentication codes to convince a legitimate node that there are many neighbor nodes in its surrounding area, and the purpose is to cause erroneous routing paths. However, the proposed mechanism pre-loads an initial certificate to ensure the legitimacy of each node. Also, the application of a new certificate requires its public key for encryption. Since the attacker does not have the private key, it can not obtain a valid certificate to deceive the other nodes.
For example, node C in Figure 19 tries to fake node A’s identity by obtaining its certificate CA and sending CA to node B. After node B sends back the certificate for identity verification, node C also fakes node B’s identification CB and send it to node A to obtain KPUB(IDA) and KPUB(IDB). Node A and node B can calculate the secret key KAB using their private keys and the other node’s public key, but node C does not have their private keys KPRI(IDA) and KPRI(IDB) , so it can not calculate the secret key KAB. If node C wants to fake a new certificate, it must obtain the base station’s private key KPRI(BS). Unless the private key KPRI(BS) is stolen or the base station is attacked, the proposed mechanism can be used for the defense against multiple identity attacks.
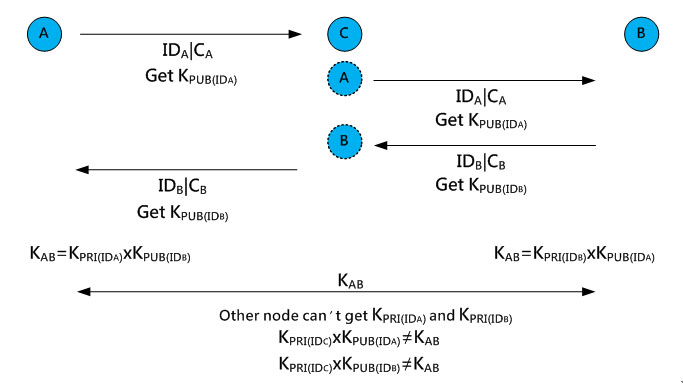
Fig. 19. Defense against multiple identity attacks
4. Conclusion
It is difficult for a symmetric key mechanism to meet the requirements of security, connectivity and scalability at the same time. As the hardware technology in sensor networks advances, ECC can be applied using a short key length for fast computation. In this study, a security mechanism based on ECC and ECDH is proposed for key management and exchange to provide authentication for identity and message transmission. Before deployment, the sensor nodes are pre-loaded with certificates such that the newly added nodes do not have to update their keys. Since the sizes of certificates and keys stored in the nodes are fixed, the number of nodes in the network will not affect the storage space. Therefore, it can be applied to a large wireless sensor network to update the certificates regularly for enhancing overall network security.
According to the security analysis, the proposed mechanism can be used for the defense against several attacks such as re-send, eavesdropping, tampering, and multiple identity attacks. Also, it is shown that the mechanism can satisfy the requirements of confidentiality, authentication and integrity. The ECC system has the advantages of lower computation complexity and higher security, so it is suitable for the applications in wireless sensor networks with P2P transmission and limited bandwidth.
This study is based on a network security analysis, and it is feasible to use real models and TinyOS Simulator (TOSSIM) to analyze the performance like computation time and power consumption as well. Due to the complexity of the PKC, there is no effective approach for the defense against blocking attacks. The authors are still working on alternative methods to simplify the computation of encryption and decryption for reducing the power consumption in wireless sensor networks.
References
| [1] | R. L. Rivest, A. Shamir, and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” Communication ACM, vol. 21, pp. 120-126, 1978. |
| [2] | V. Miller, “Use of Elliptic Curves in Cryptography,” Advances in Cryptology - CRYPTO '85: Proceedings, pp. 417-426, 1986. |
| [3] | N. Koblitz, “Elliptic Curve Cryptosystems,” Mathematics of Computation, vol. 48, pp. 203-209, 1987. |
| [4] | S. Vanstone, “Responses to NIST’s proposal,” Communication ACM, vol. 35, pp. 50-52, 1992. |
| [5] | N. Gura, A. Patel, A. Wander, H. Eberle, and S. C. Shantz, “Comparing Elliptic Curve Cryptography and RSA on 8-bit CPUs,” Cryptographic Hardware and Embedded Systems - CHES 2004, pp. 925-943, 2004. |
| [6] | D. J. Malan, M. Welsh, and M. D. Smith, “A public-key infrastructure for key distribution in TinyOS based on elliptic curve cryptography,” Proceedings of Sensor and Ad Hoc Communications and Networks, pp. 71-80, 2004. |
| [7] | W. Ronald, K. Derrick, C. Sue-fen, G. Charles, L. Charles, and K. Peter, “TinyPK: securing sensor networks with public key technology,” Proceedings of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks Washington DC, USA: ACM, 2004. |
| [8] | P. Krzysztof, L. Peter, and P. Steffen, “How public key cryptography influences wireless sensor node lifetime,” Proceedings of the fourth ACM workshop on Security of Ad Hoc and Sensor Networks Alexandria, Virginia, USA: ACM, 2006. |
| [9] | W. R. Heinzelman, A. Chandrakasan, and H. Balakrishnan, “Energy-efficient communication protocol for wireless microsensor networks,” Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, 2000. |
| [10] | M. J. Handy, M. Haase, and D. Timmermann, “Low energy adaptive clustering hierarchy with deterministic cluster-head selection,” 4th International Workshop on Mobile and Wireless Communications Network, pp. 368-372, 2002. |
| [11] | A. Manjeshwar and D. P. Agrawal, “TEEN: a routing protocol for enhanced efficiency in wireless sensor networks,” 15th International Parallel and Distributed Processing Symposium, pp. 2009-2015, 2001. |
| [12] | A. Manjeshwar and D. P. Agrawal, “APTEEN: a hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks,” International Parallel and Distributed Processing Symposium, pp. 195-202, 2002. |
| [13] | R. D. John, “The Sybil Attack,” Revised Papers from the First International Workshop on Peer-to-Peer Systems: Springer-Verlag, 2002. |
| [14] | L. Donggang and N. Peng, “Establishing pairwise keys in distributed sensor networks,” Proceedings of the 10th ACM Conference on Computer and Communications Security Washington D.C., USA: ACM, 2003. |
| [15] | A. Fernandes, “Elliptic Curve Cryptography,” Dr. Dobb's Journal, December 1999. |
| [16] | Standards for Efficient Cryptography Group, SEC 1: Elliptic Curve Cryptography, version 1.0, 2000. Available at http://www.secg.org |
Biographies
 Cheng-Lung Yang received his B.S. degree in computer and information science
from Aletheia University, Taiwan in 2007, and M.S. degree in computer science
from National Hsinchu University of Education, Taiwan in 2009. His research
interests include network security and wireless sensor networks.
Cheng-Lung Yang received his B.S. degree in computer and information science
from Aletheia University, Taiwan in 2007, and M.S. degree in computer science
from National Hsinchu University of Education, Taiwan in 2009. His research
interests include network security and wireless sensor networks.
 Wernhuar Tarng is a professor in the Institute of Computer Science, National
Hsinchu University of Education, Taiwan. He received his M.S. and Ph.D. degrees
in electrical and computer engineering from State University of New York at
Buffalo, USA in 1987 and 1992, respectively. He was a visiting scholar at the
Distance and Online Learning Center of Oxford University, UK in 2003. His
research interests include computer network, real-time systems, e-learning, and
virtual reality.
Wernhuar Tarng is a professor in the Institute of Computer Science, National
Hsinchu University of Education, Taiwan. He received his M.S. and Ph.D. degrees
in electrical and computer engineering from State University of New York at
Buffalo, USA in 1987 and 1992, respectively. He was a visiting scholar at the
Distance and Online Learning Center of Oxford University, UK in 2003. His
research interests include computer network, real-time systems, e-learning, and
virtual reality.
 Kuen-Rong Hsieh received his M.S. and Ph.D. degree in computer science from
National Tsing Hua University, Taiwan, in 1986 and 1992, respectively. Currently,
he is a Senior Manager with Ralink Technologies, Taiwan. His research interests
include networking, security, and wireless communication.
Kuen-Rong Hsieh received his M.S. and Ph.D. degree in computer science from
National Tsing Hua University, Taiwan, in 1986 and 1992, respectively. Currently,
he is a Senior Manager with Ralink Technologies, Taiwan. His research interests
include networking, security, and wireless communication.
 Mingteh Chen received his Ph.D. degree in electrical and computer engineering
from State University of New York at Buffalo, USA in 1996. He first started at
Toshiba working on MIPS 5900 CPU processor for SONY PlayStation II. In 1998,
he joined Nortel Network to develop Ethernet Layer 3 Switch/Router ASIC targeted
enterprise level market. While at a startup, he was the manager leading SoC projects,
and developed the world first ARM9 based SoC Router. He is currently with Micrel
Inc, managing an SoC design team to develop VoIP SoC products.
Mingteh Chen received his Ph.D. degree in electrical and computer engineering
from State University of New York at Buffalo, USA in 1996. He first started at
Toshiba working on MIPS 5900 CPU processor for SONY PlayStation II. In 1998,
he joined Nortel Network to develop Ethernet Layer 3 Switch/Router ASIC targeted
enterprise level market. While at a startup, he was the manager leading SoC projects,
and developed the world first ARM9 based SoC Router. He is currently with Micrel
Inc, managing an SoC design team to develop VoIP SoC products.


